**Kindly contact support if you need technical assistance to set up an On-Premise VPN Server (Access Gateway)**
The following guide will walk you through the steps involved in creating a UTunnel On-Premise VPN Server or Gateway.
1. Log in to your UTunnel account (Organization/Personal) and navigate to the CREATE button in the Create an Access Gateway section.
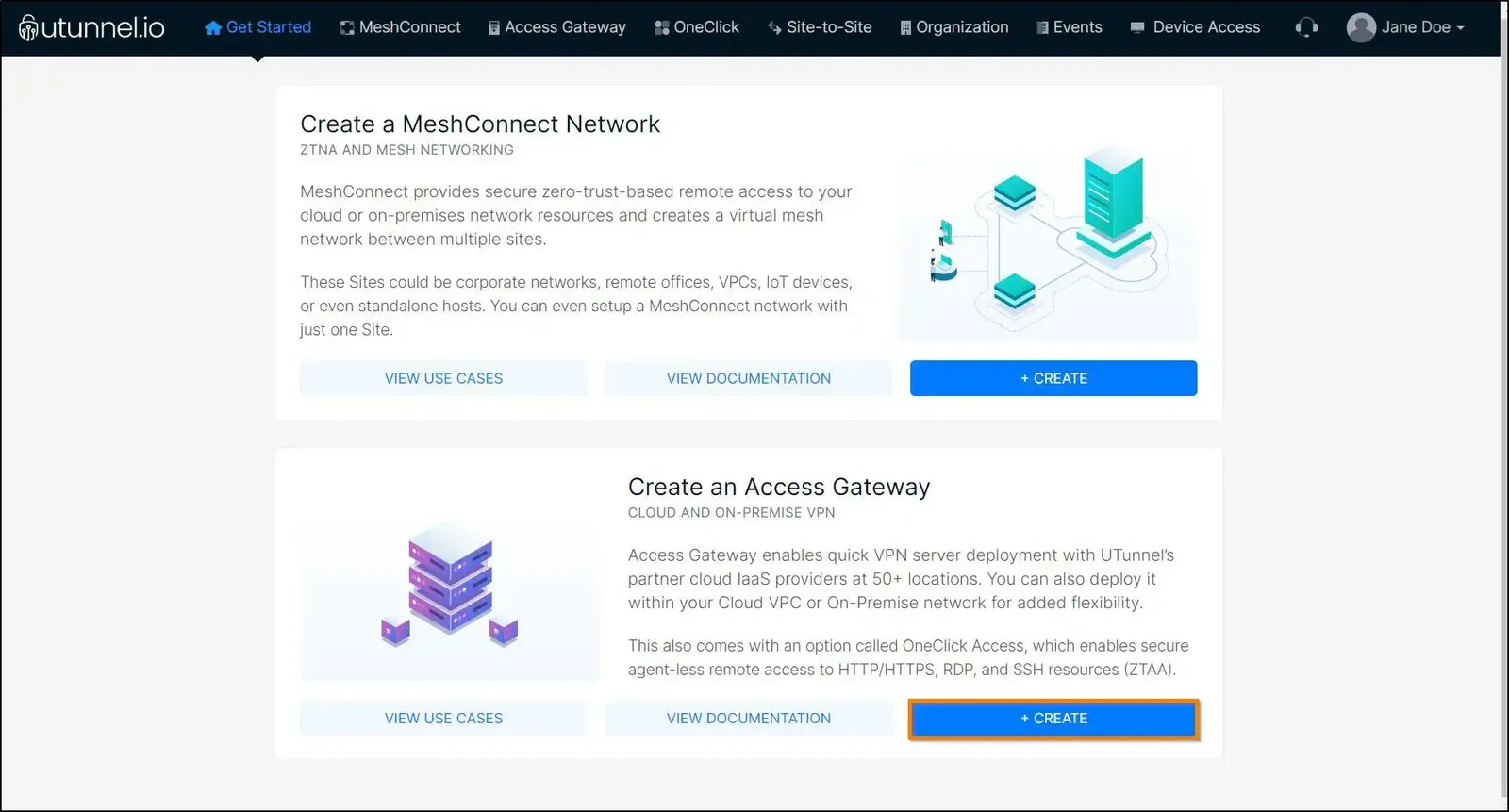
2. The next step is to select the On-Premise option and enter the Access Gateway details as given below:
After configuring your Access Gateway specifications, click on the Proceed button.
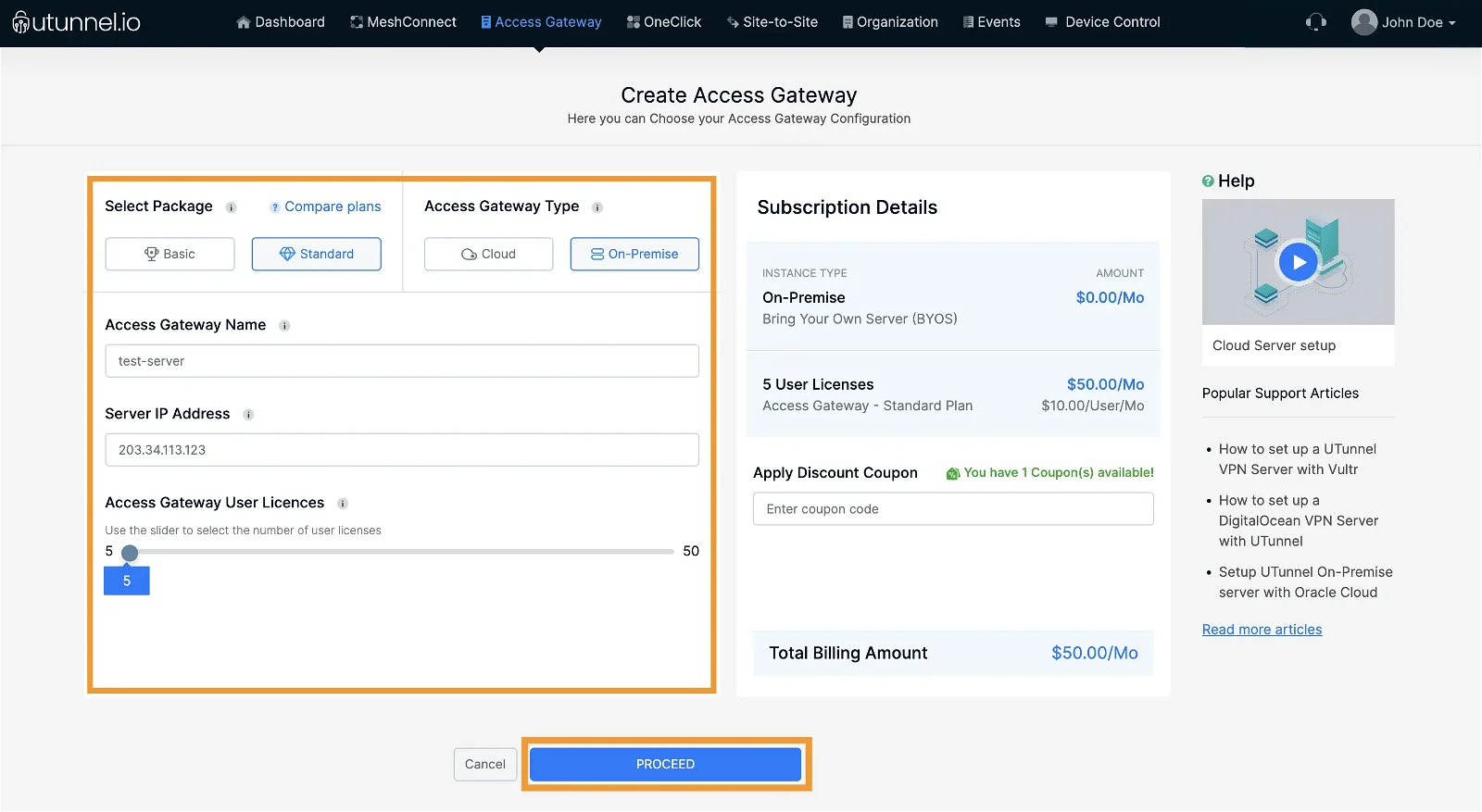
3. You will reach the Order Summary page, which displays the details of the Access Gateway configuration and the billing amount. Click on the Proceed button to make the payment.
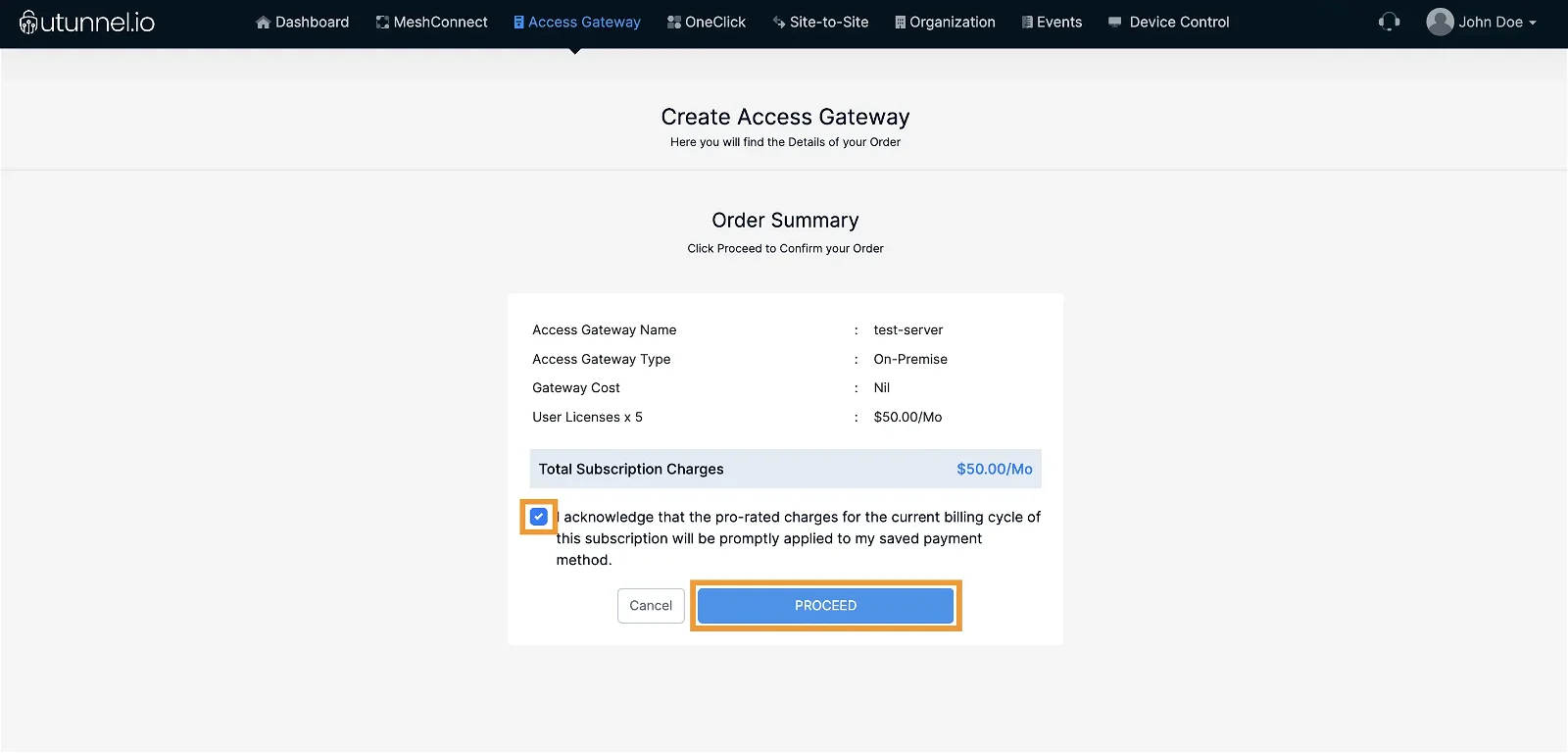
4. If this is your first subscription, you will be asked to enter your credit card details. In that case, enter your payment details and click the Start Your Trial button.
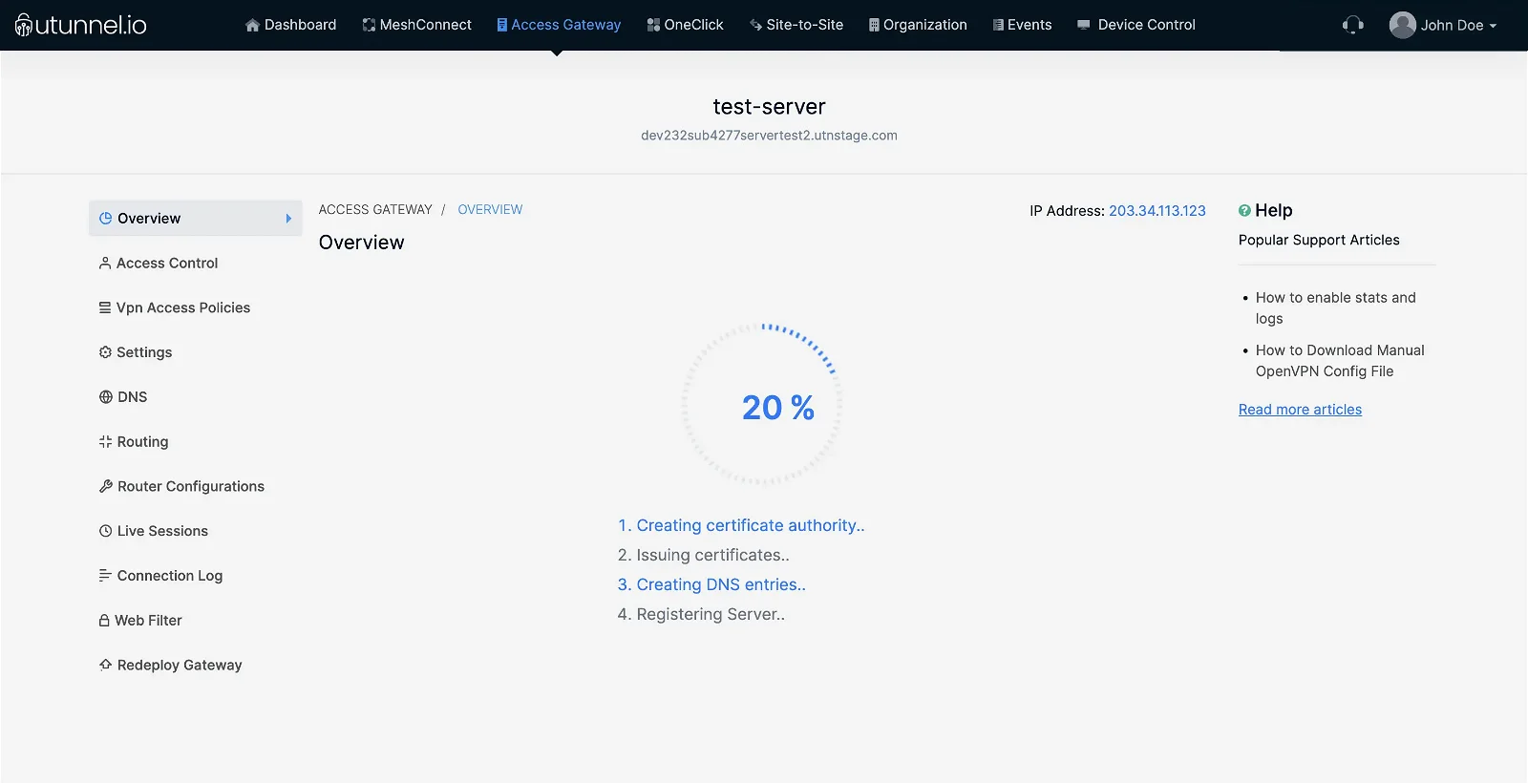
5. You will be directed to the Access Gateway Overview page, where you can check the VPN server creation status.
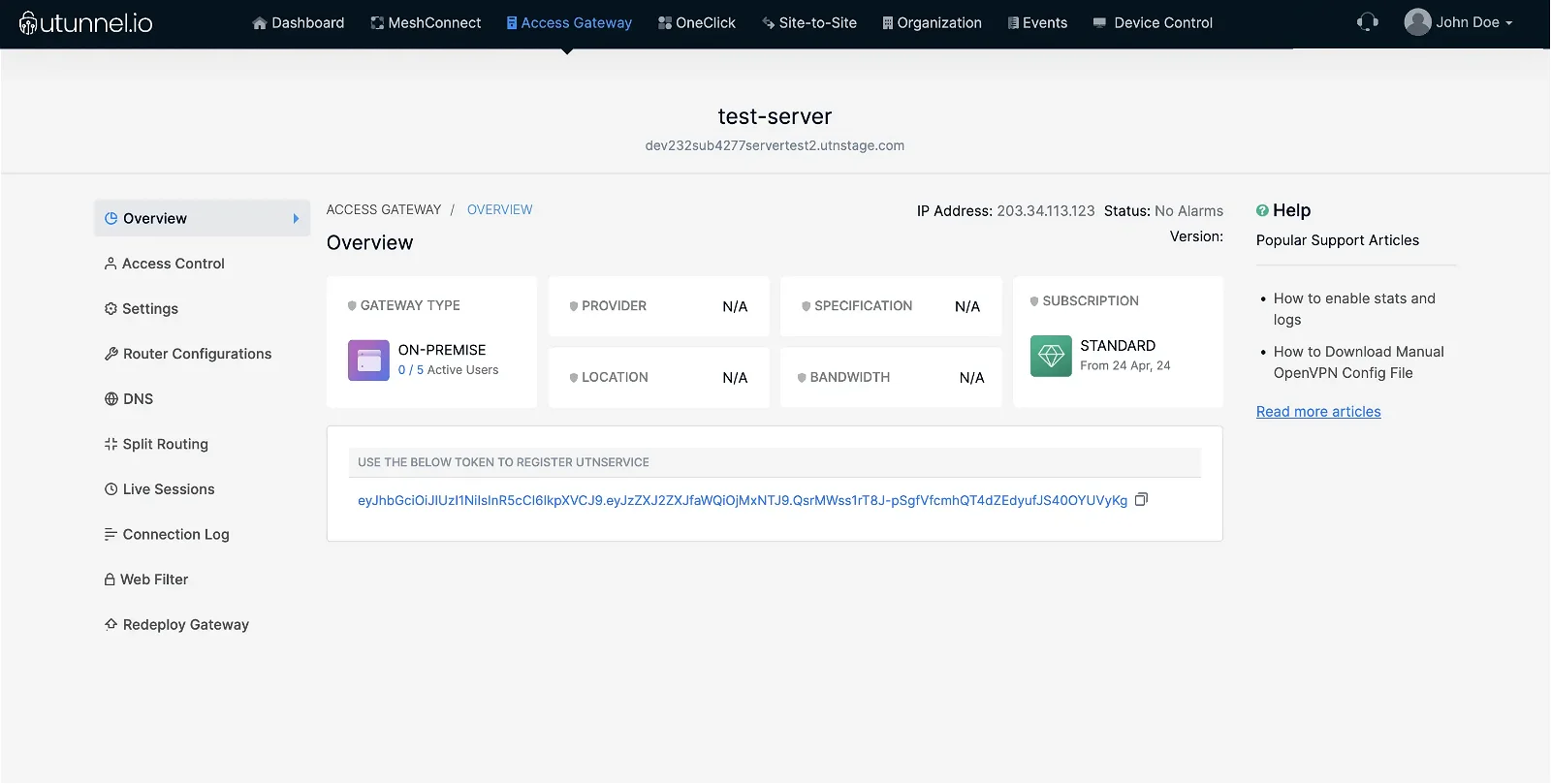
6. You will be directed to the Access Gateway Overview page, where the registration token is displayed. Please copy the registration token as it is required when you deploy the access gateway
7. Now it's time to connect to your server via SSH. You will need sudo access to complete the below steps. After the successful login, execute the following commands.
First, disable the default firewall rules. UTunnel will load it's own firewall rules automatically.
Now go ahead and run the following commands.
In the next command, you need to replace YOUR_REG_TOKEN with the registration token you copied from the Access Gateway Overview page.
Now it's the time to start UTunnel Service on your server. Run following command for the same.
8. Make sure that inbound connections to the following ports are allowed to accept VPN connections.
Ports used for OpenVPN connections:
Ports used for IPSEC connections:
Ports used for managing UTunnel services like live sessions, firewalls, and site-to-site tunneling:
Now your Access Gateway will be ready to accept a VPN connection. Invite users to your Access Gateway and start using a VPN.
**Kindly contact support if you need technical assistance to set up your On-Premise VPN Gateway**