This guide will help you on how to configure OneLogin to provide SSO for UTunnel VPN using SAML.
1. Log in to OneLogin and go to Applications > Applications.
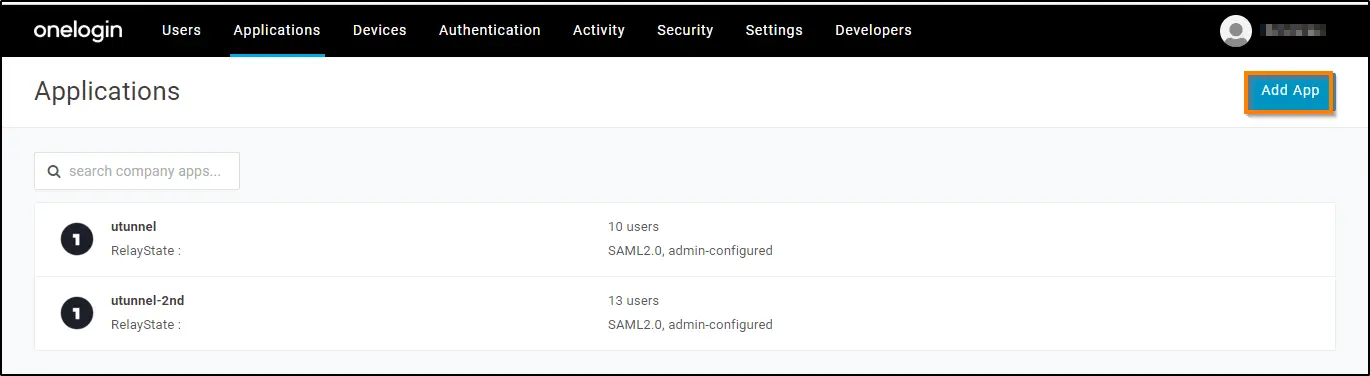
2. Click ADD APP to add your connector.
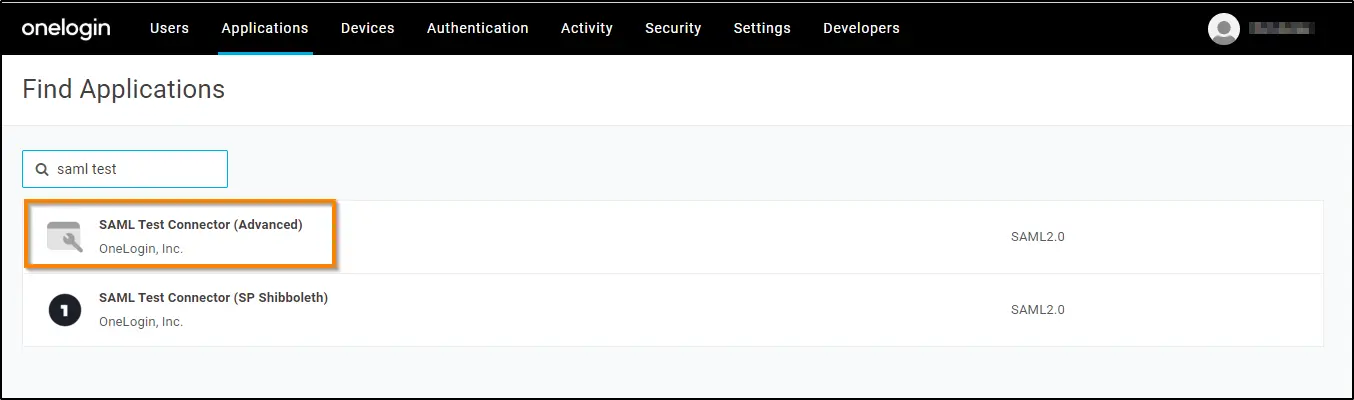
3. Search SAML TEST in the search tab. Select SAML TEST Connector (Advanced) from the list.
4. Click on the Save button to add the app to your Company Apps and display additional configuration tabs.
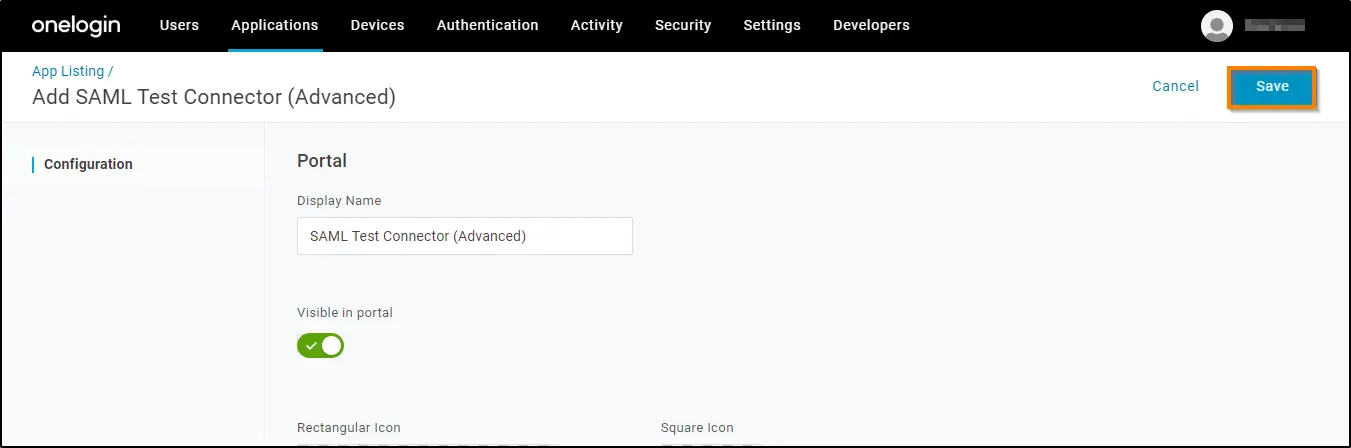
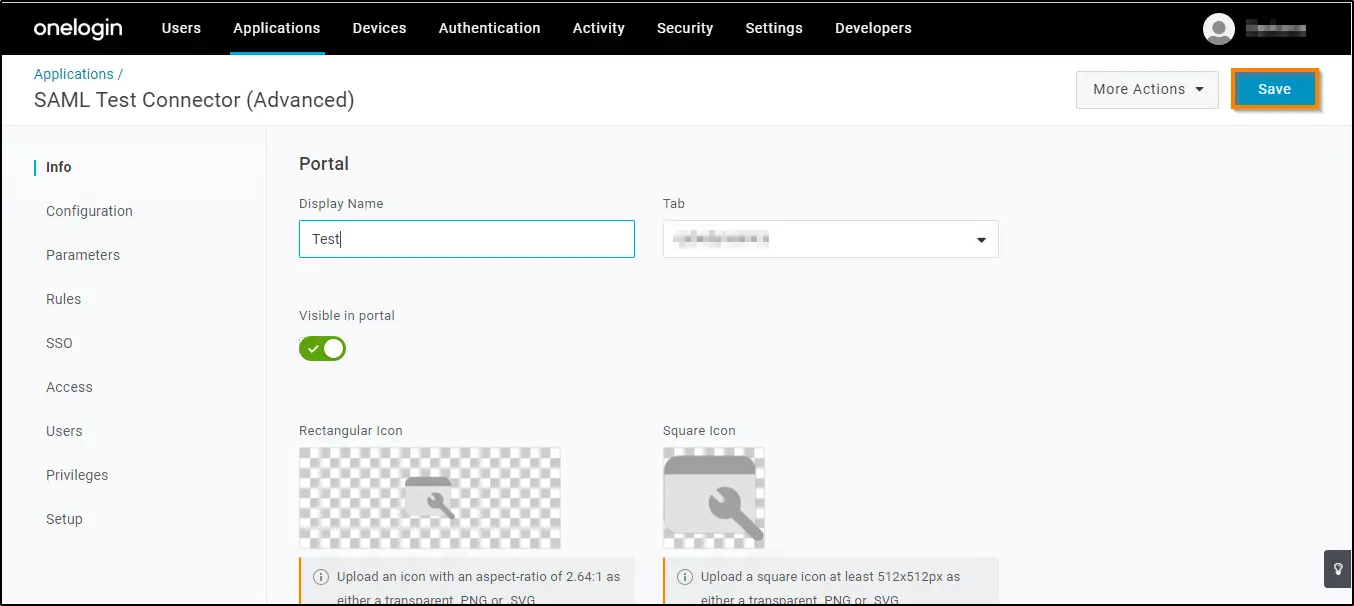
5. You can provide any preferred name in the Display Name field. Click on the Save button.
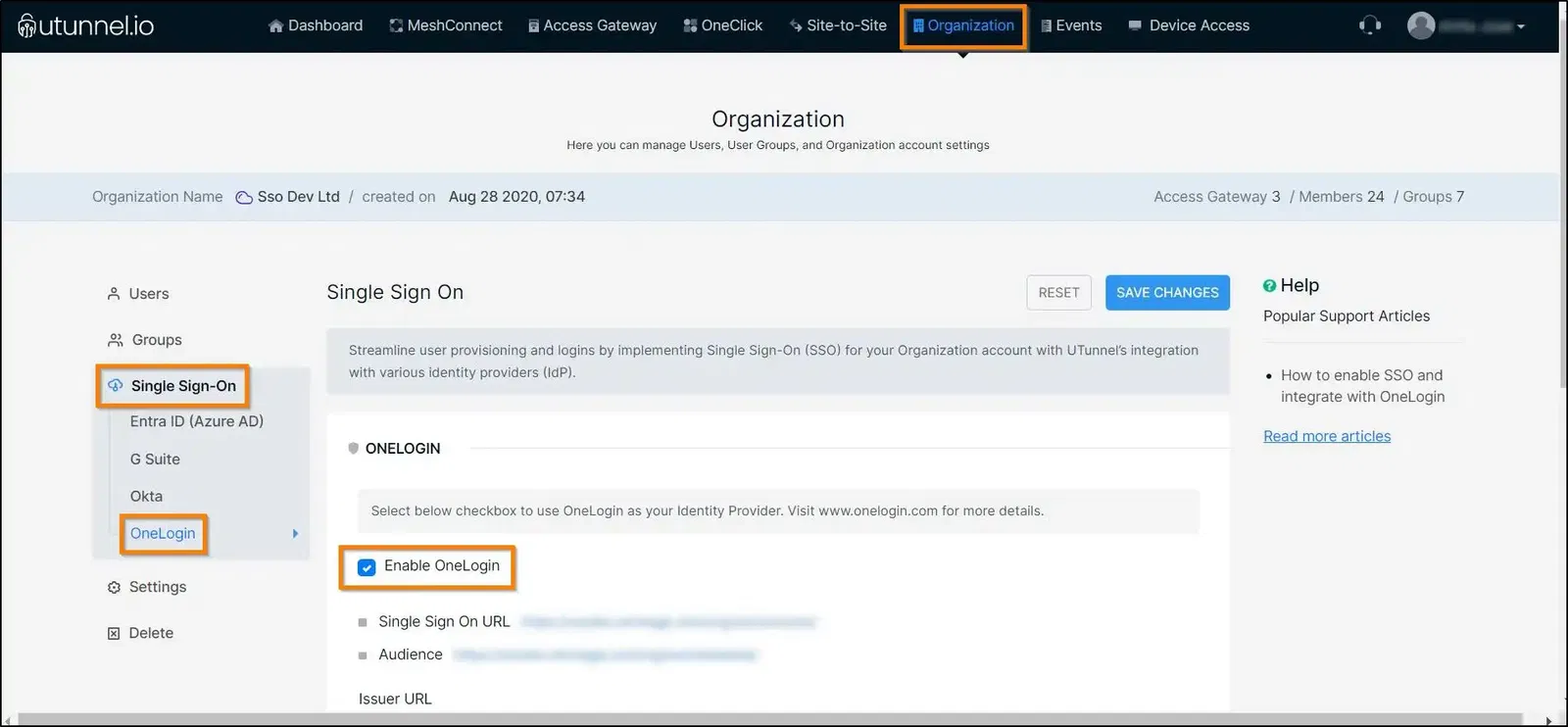
6. Next step is Configuration. Select the Configuration tab and keep it ready. To configure, navigate to your UTunnel dashboard and select the Organization tab from the top menu. Click on the Single Sign On tab from the left menu and select OneLogin. Click on the Enable OneLogin checkbox. Ensure that this page is kept open as we need it in the following steps.
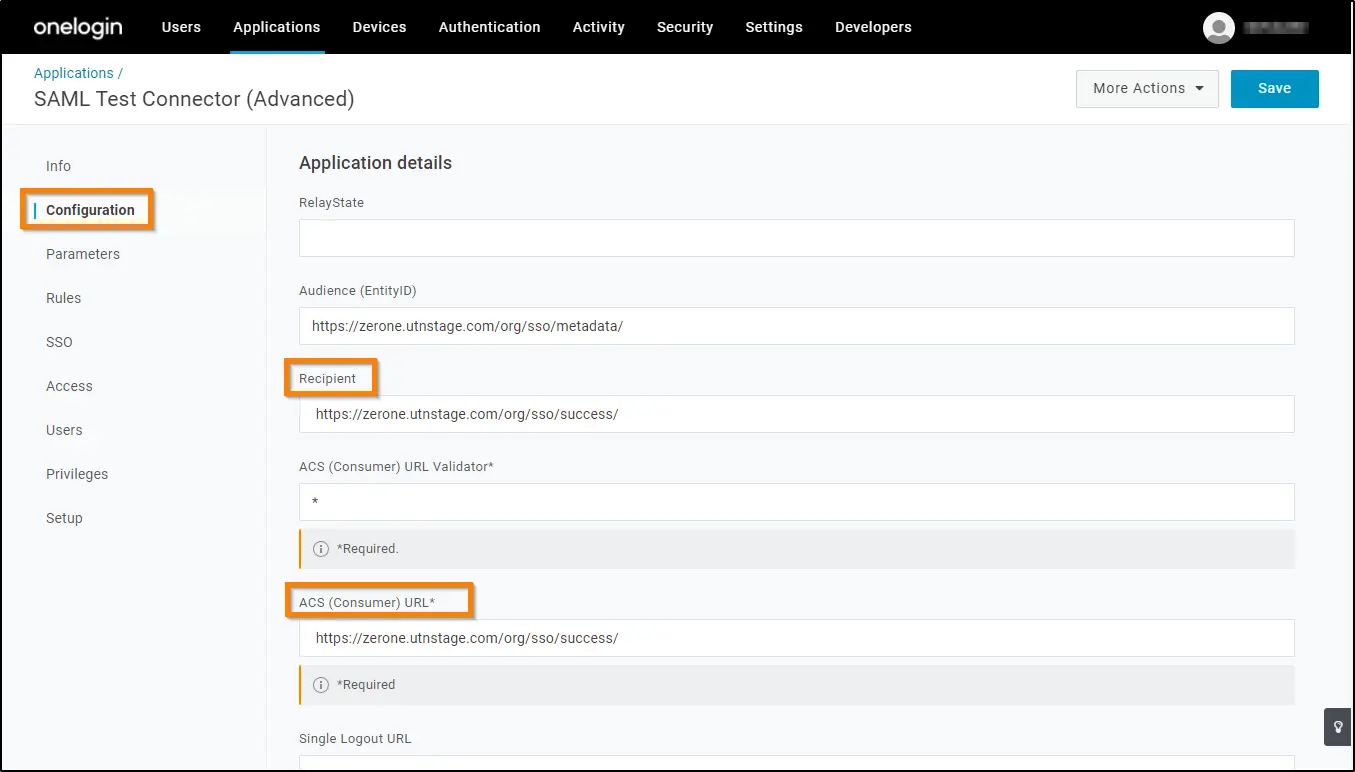
7. Copy the Single Sign On URL from the Single Sign On screen and paste it on the Recipient, ACS (Consumer) URL* and Login URL fields in the Configuration screen in the Configuration tab.
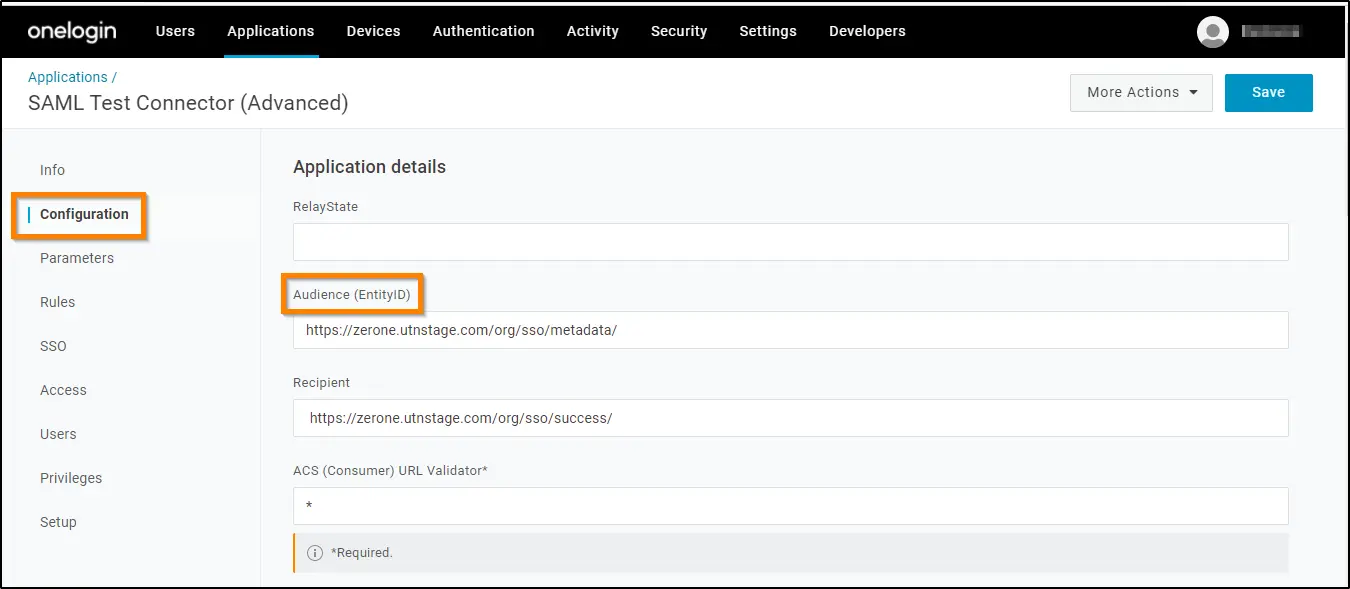
8. Now copy the URL next to Audience on the Single Sign On screen and paste it on the Audience field in the Configuration screen. Click on the SAVE button.
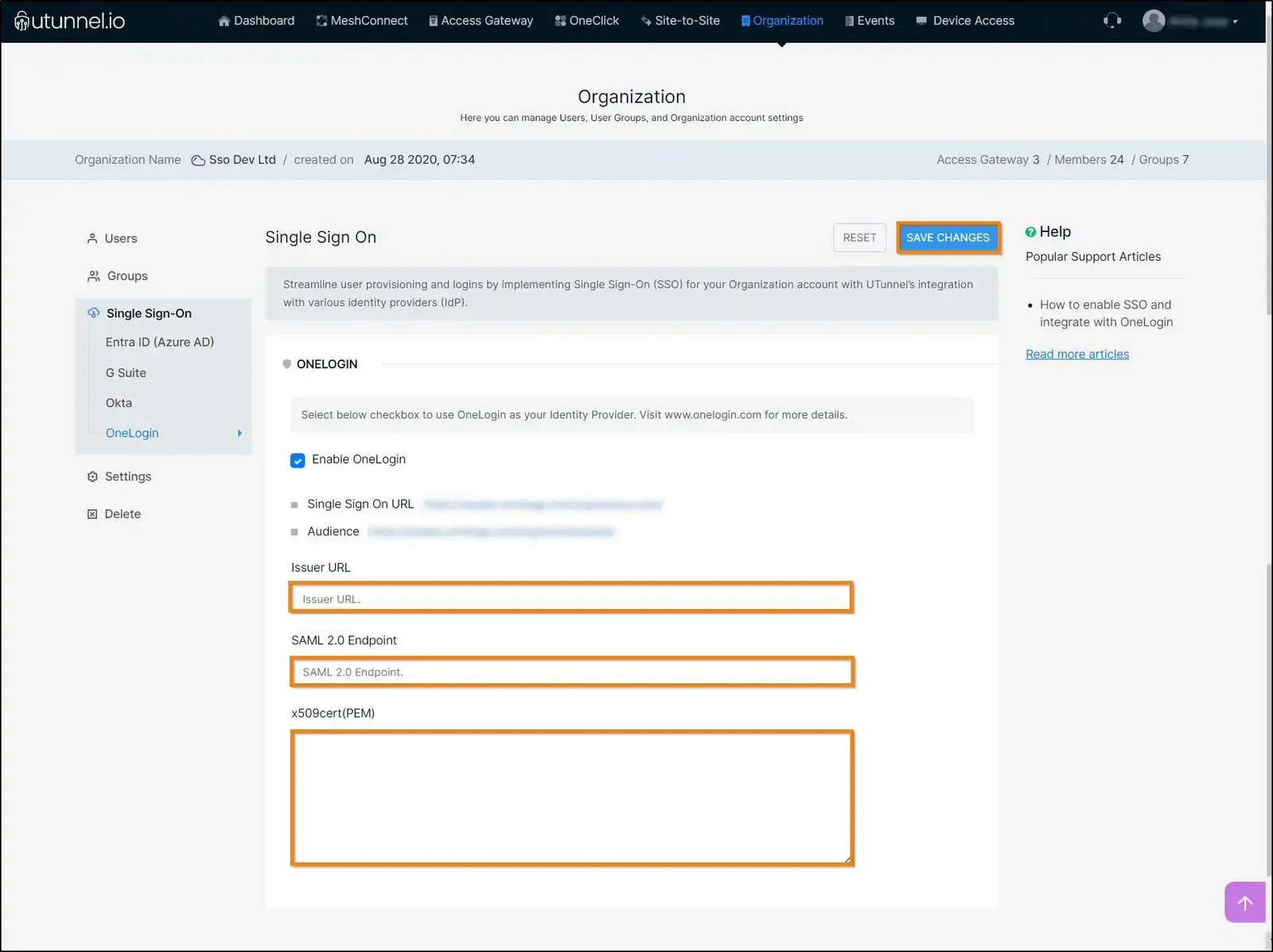
9. On the SSO tab, copy the two SAML values: SAML 2.0 Endpoint (HTTP) and X.509 Certificate and Issuer URL that you'll need to provide on your UTunnel OneLogin section.
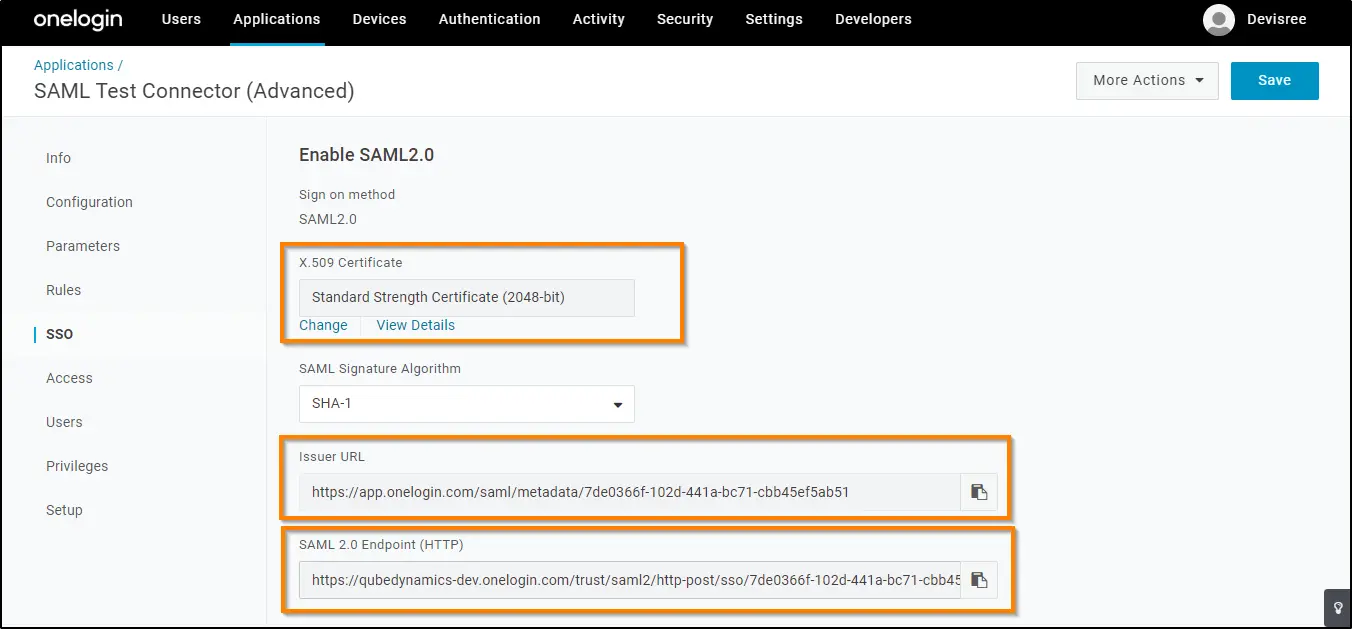
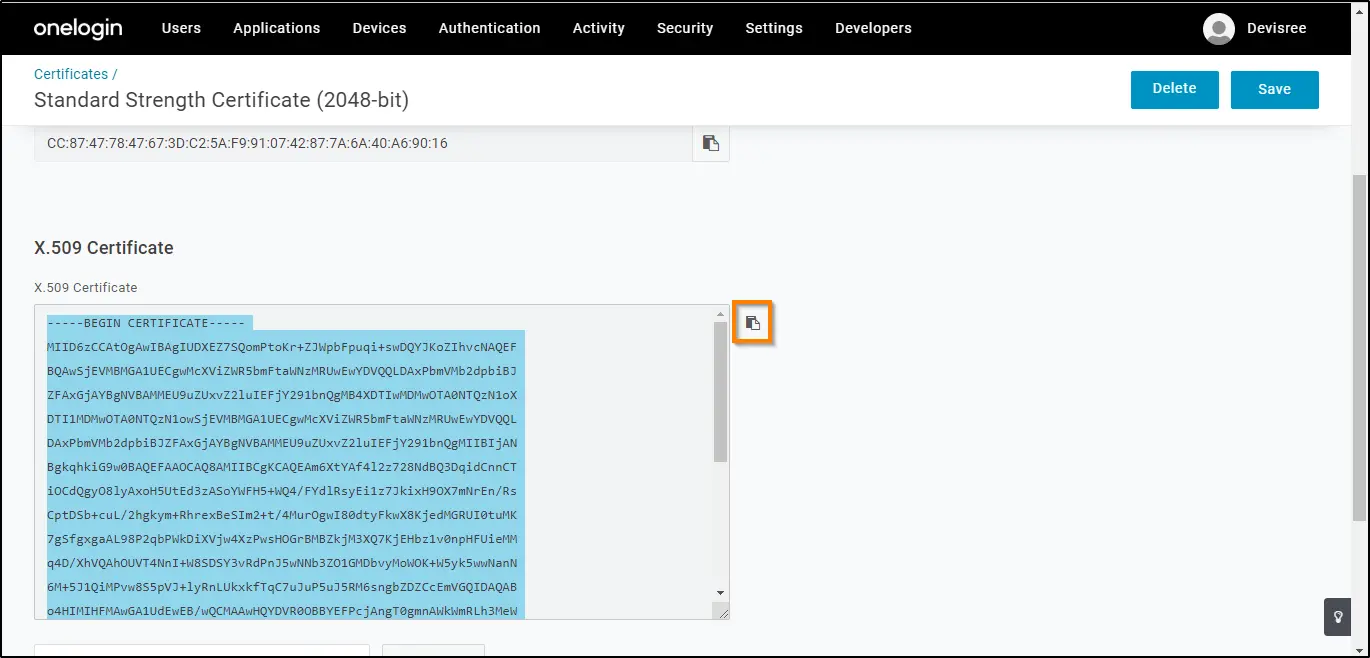
10. To copy the X.509 certificate, click View Details. Then, click the Copy to Clipboard icon for the X.509 Certificate.
11. Paste all three SAML values into the corresponding fields on the SSO screen and click on the SAVE CHANGES button.
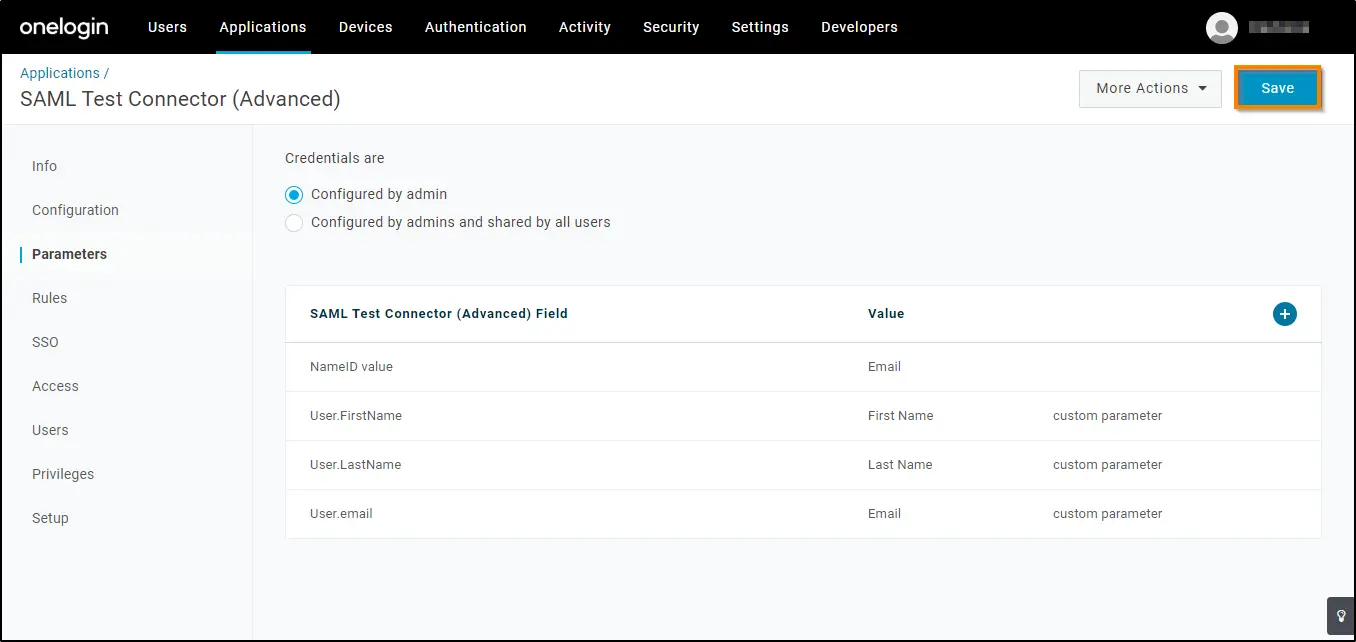
12. Now access the Parameters tab. You need to map UTunnel user attributes to OneLogin attributes. Click the Add (+) button. Enter each attribute in the Field name and click the Save button and select the corresponding values as given below and click the Save button. Ensure you copy and paste as given below because the attributes are case-sensitive. Click Save to effect the changes.
|
Field Name attributes
|
Value
|
Now you have enabled SSO and integrated your UTunnel Organization account with OneLogin. You can now add users to your OneLogin account and grant them permission to access UTunnel VPN.