This guide describes how to deploy and manage an Exoscale VPN gateway using UTunnel's Cloud VPN as a Service.
UTunnel facilitates quick and easy VPN server deployment with many leading IaaS providers, including Exoscale. UTunnel’s hassle-free VPN gateway deployment process makes it easy for users to deploy and manage a VPN gateway with Exoscale.
1. Log in to your Exoscale account and create a Virtual Private Server on the Exoscale portal. While creating the VPS, make sure that you select Ubuntu 20.04 server.
2. After creating the Exoscale VPS, copy and note down the newly created instance’s IP address.
3. Create a UTunnel account and log in to your account. Navigate to the CREATE button in the Create an Access Gateway section.
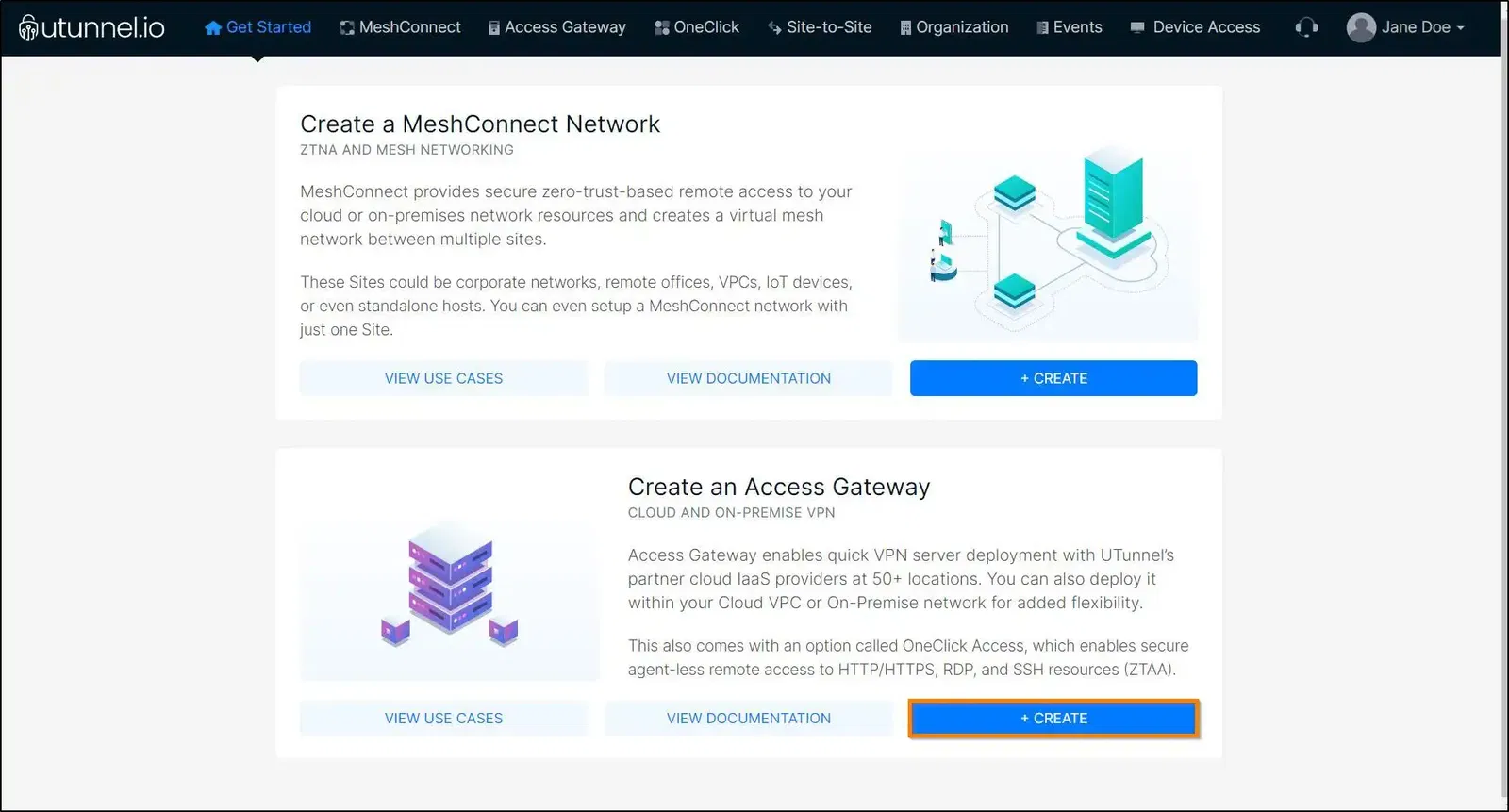
4. Fill in your billing address and click on the PROCEED button to move to the next step. You can also skip this step by clicking on the Skip button.
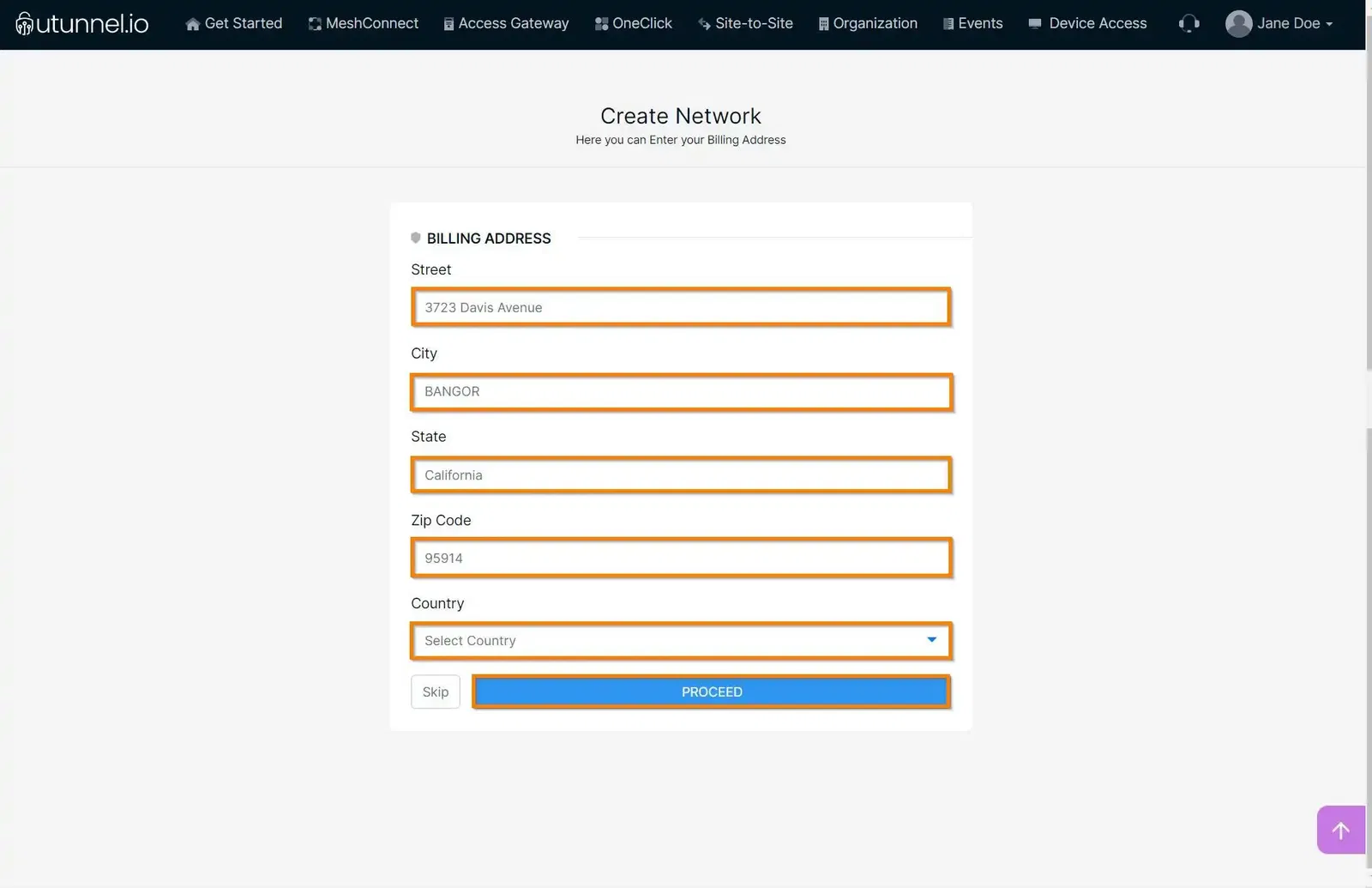
5. You can customize your Exoscale VPN gateway by managing the following options:
Click on the PROCEED button once you finish customizing the Accesss Gateway configurations to proceed to the next step.
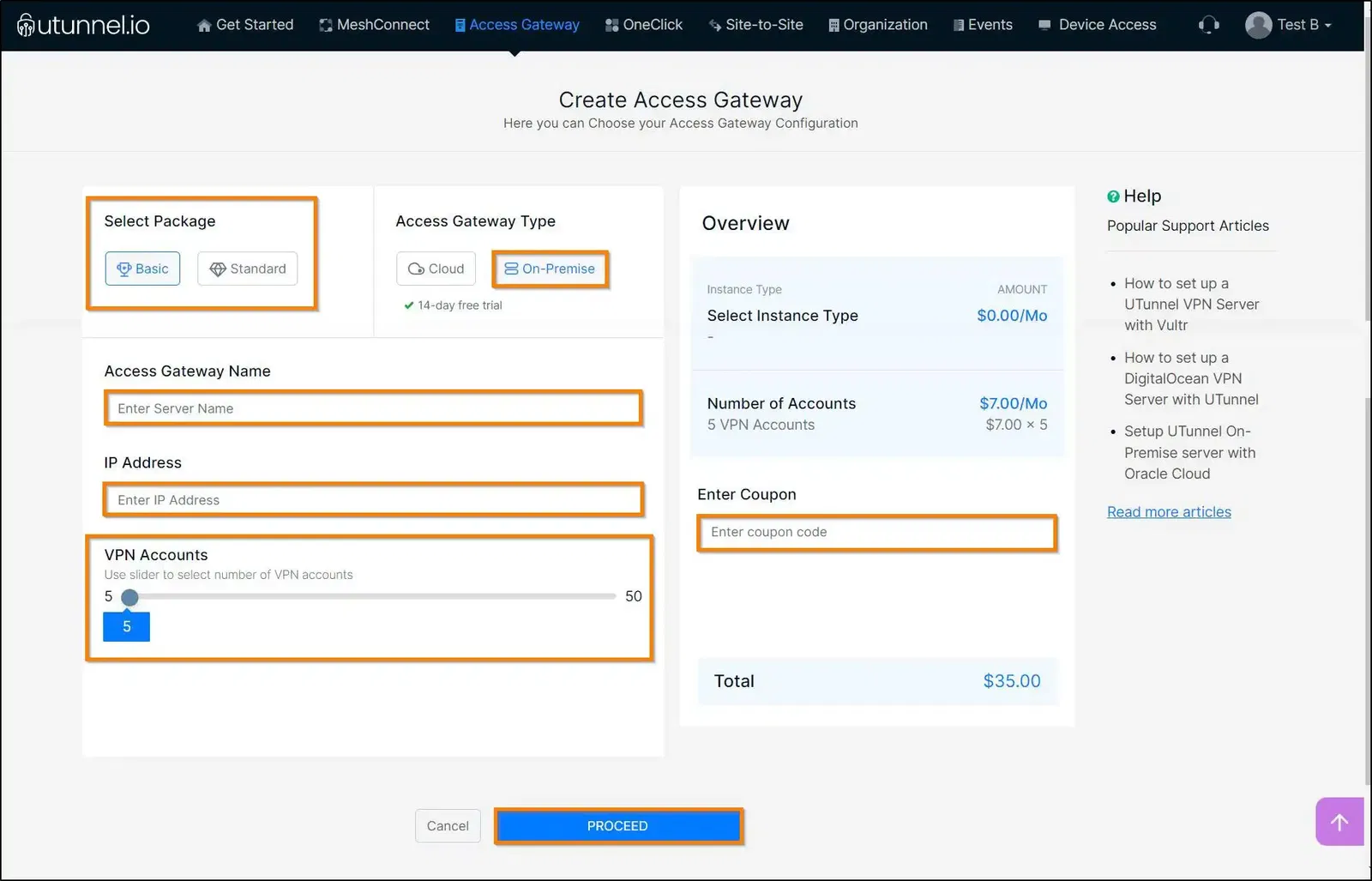
6. You can review your Access Gateway details on the Order Summary page. Click on the PROCEED button to progress to the next step.
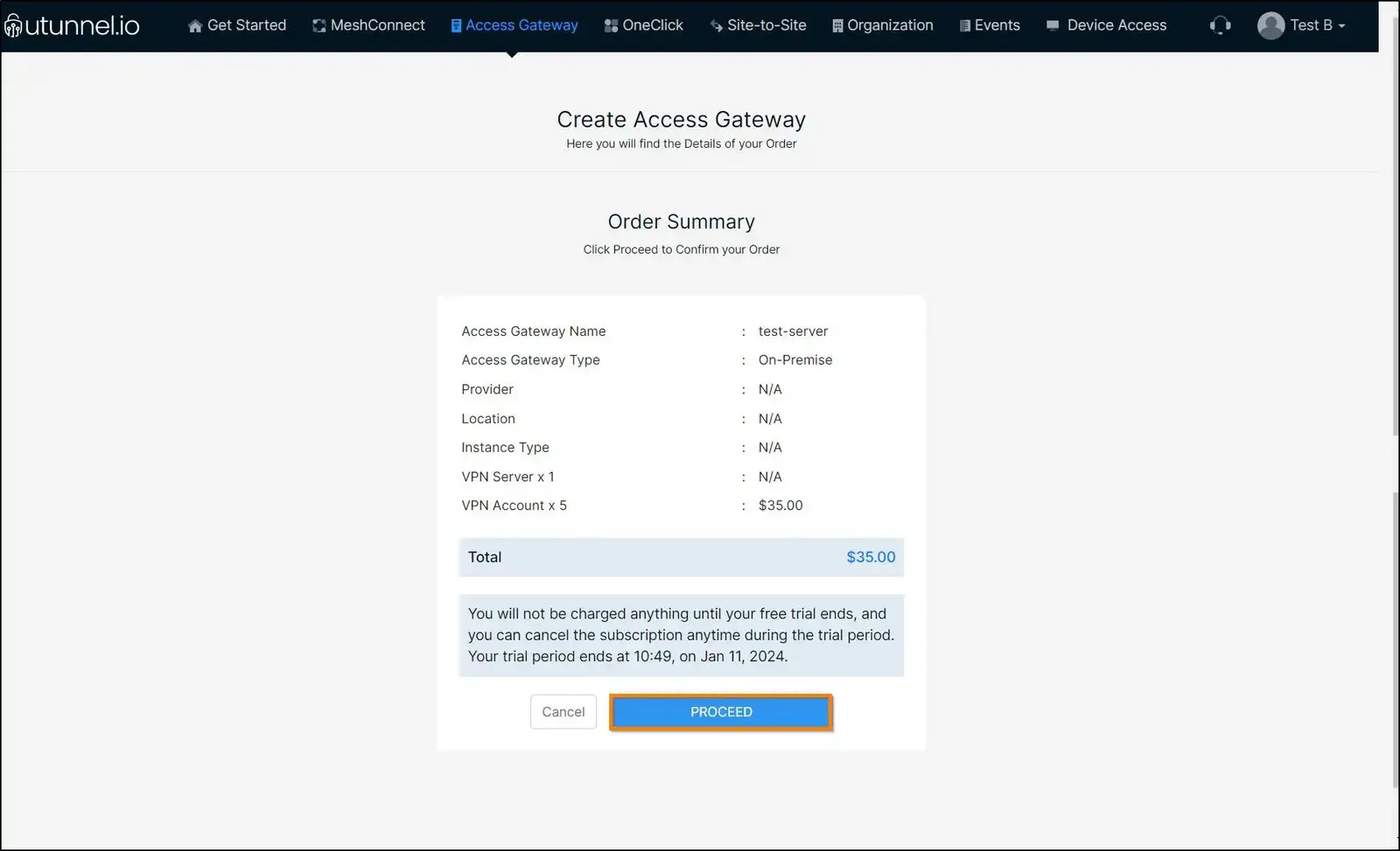
7. Enter your credit card details as required and click on the Start Your Trial/Pay Now button to initiate the Access Gateway creation.
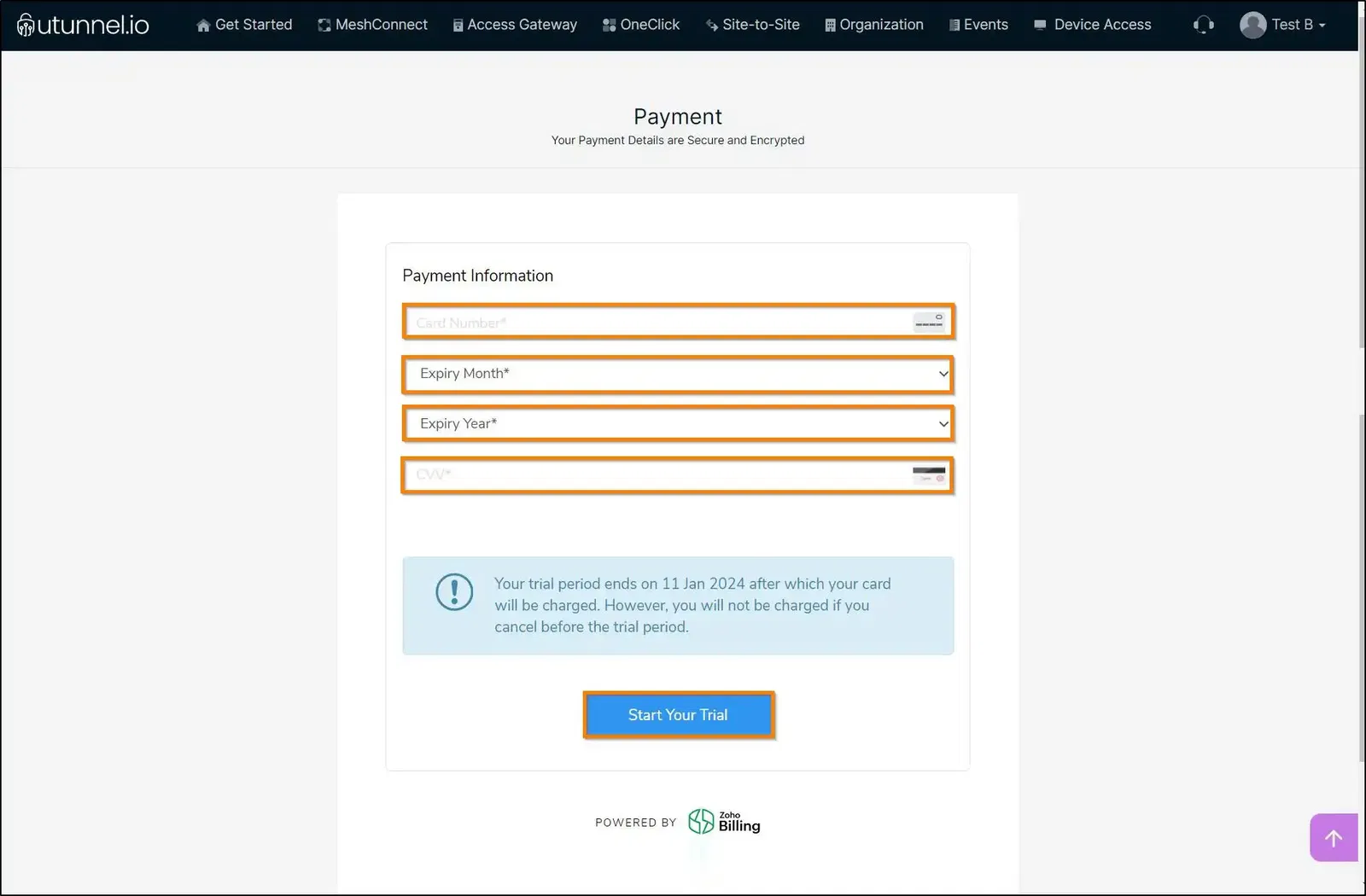
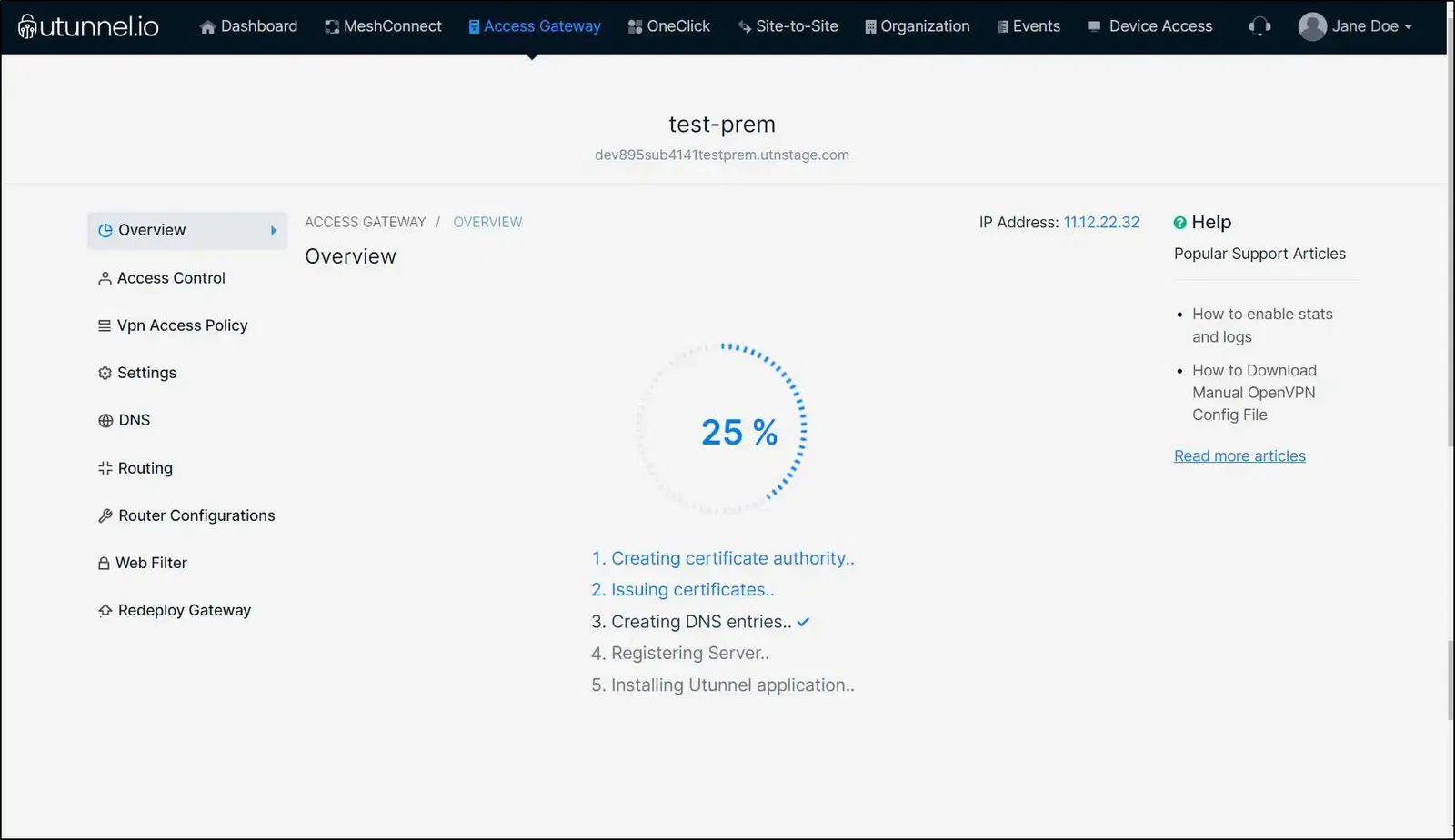
8. You will be directed to the Access Gateway Overview page where you can check the Access Gateway deployment status.
9. Once the Access Gateway deployment is initiated, you will get a registration token, which you need to register your Exoscale VPN gateway.
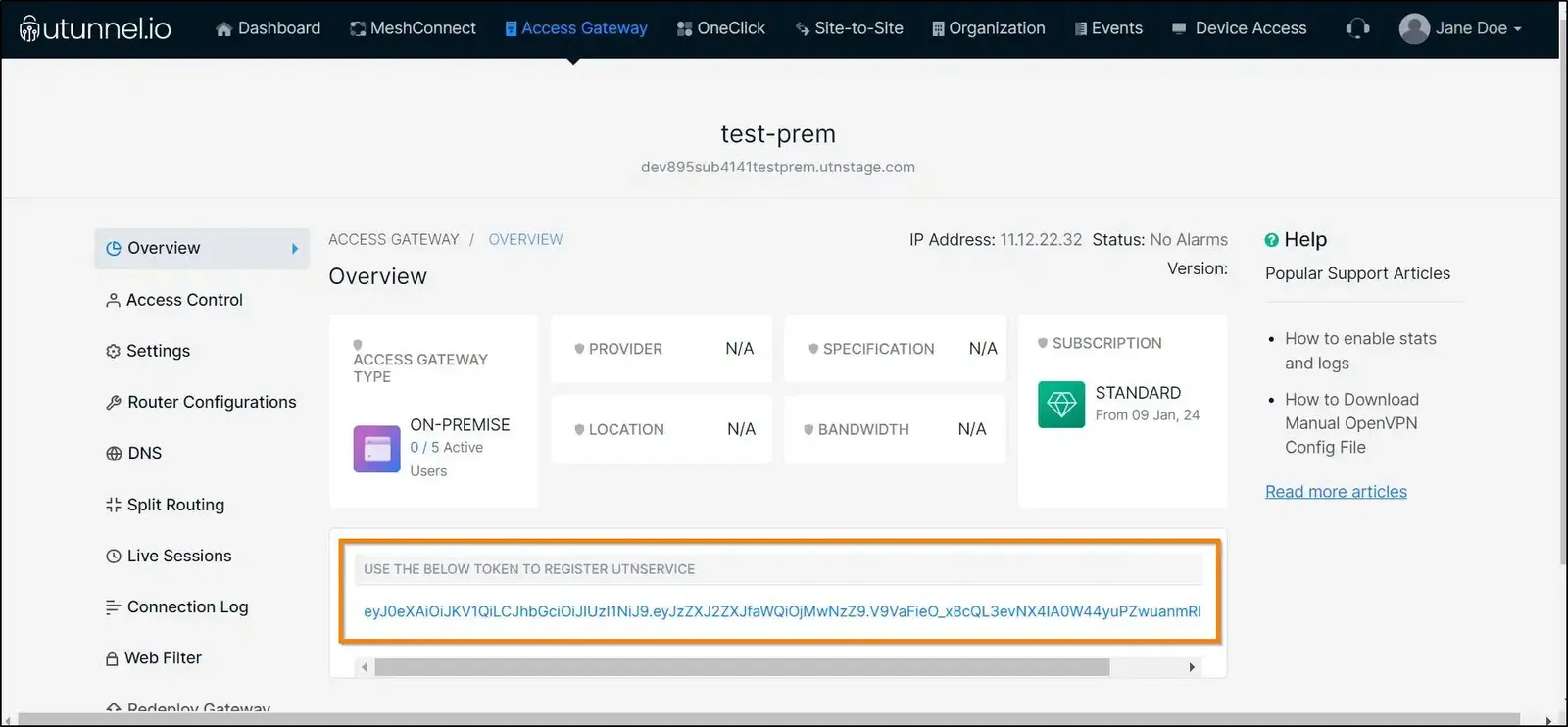
10. To execute the next steps to deploy your Exoscale VPN gateway, your need to connect to your server via SSH and run the following commands. You need to have sudo access to run these commands.
Create a directory named utunnel and make it the current working directory:
Download the required files and extract them with the command:
Register your Exoscale VPN gateway after replacing YOUR_REG_TOKEN with the registration token you received earlier
Now start the VPN service with the command:
11. You also have to make sure that inbound connections to the following ports are allowed to accept VPN connections.
Ports used for OpenVPN connections
Ports used for IPSEC connections
Ports used for managing UTunnel services like live sessions, firewall, and site-to-site tunneling.
Now your Exoscale VPN gateway is ready for use. You can invite users into your Access Gateway and start using the VPN.