To create a site-to-site tunnel between UTunnel VPN server and Sophos firewall, you will need to meet the following prerequisites.
Once the prerequisites are ready, login to your UTunnel dashboard and click on ‘Site-to-Site‘ option from top center.
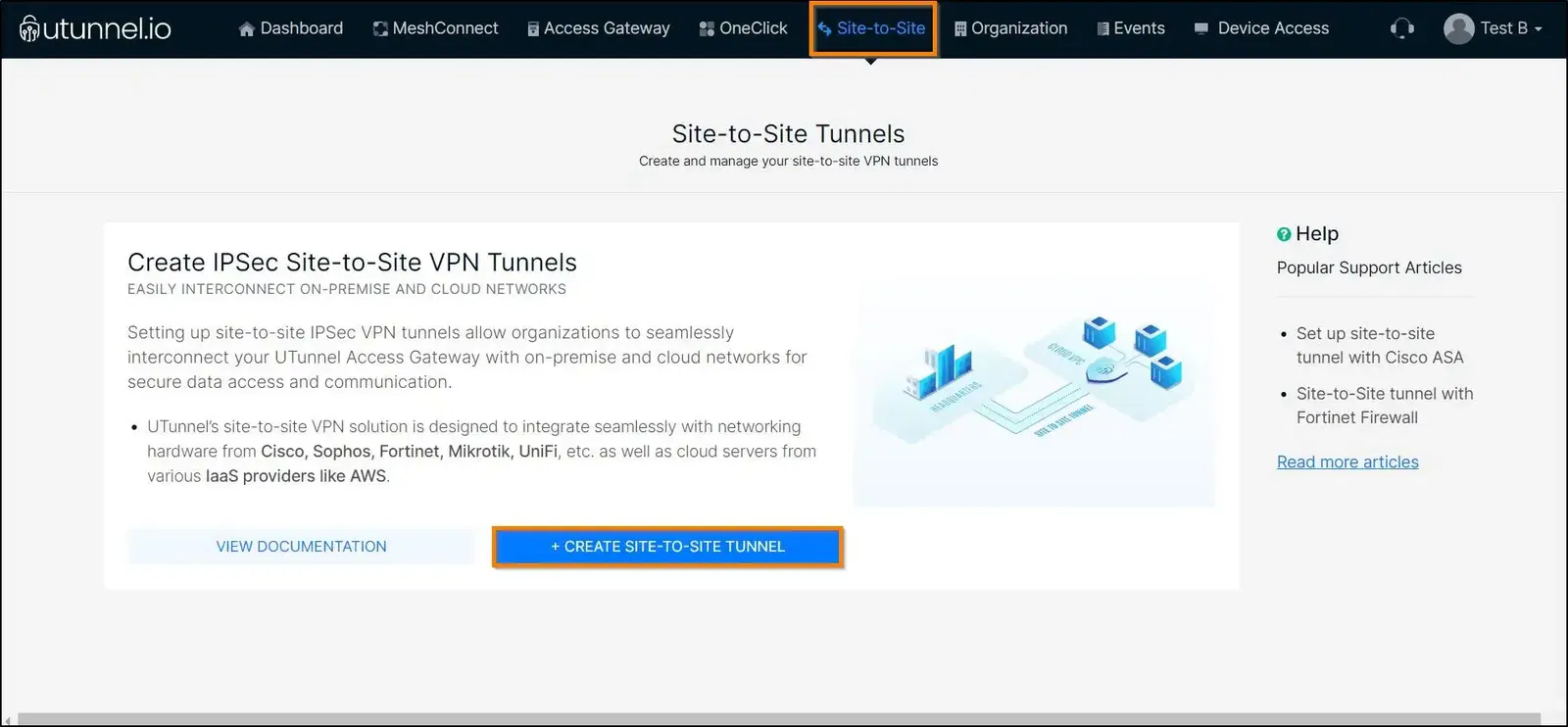
Select the option TUNNEL WITH NON UTUNNEL SERVER
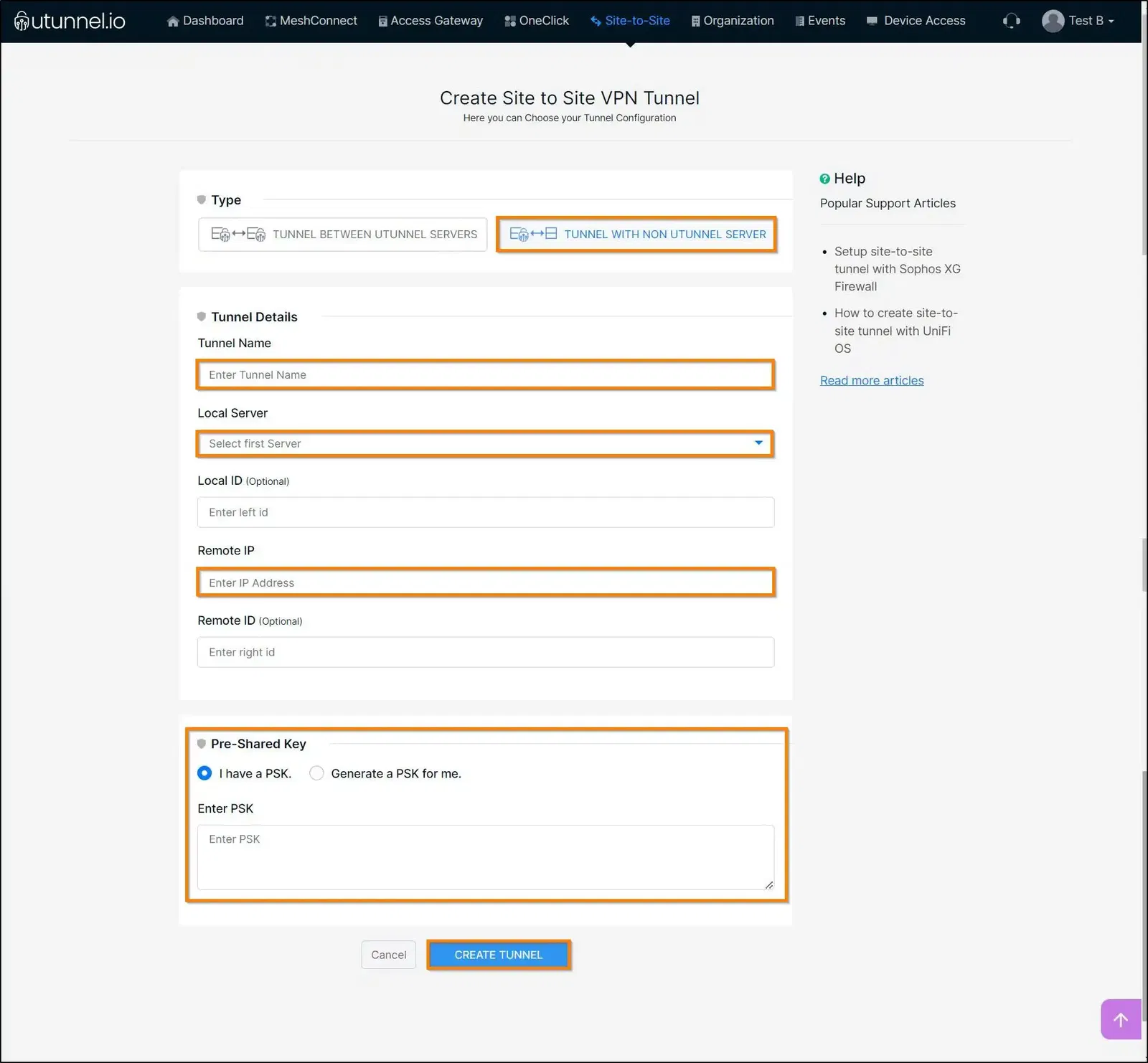
Select the option ‘TUNNEL BETWEEN REMOTE ENDPOINTS’ and key in the configuration parameters are described below.
Tunnel Name: A name for this tunnel.
Local Server: Select the UTunnel server (if you have multiple UTunnel servers) from the dropdown for which you want to create the VPN tunnel.
Remote IP: Sophos's Public IP address.
PSK: UTunnel uses Preshared key for tunnel authentication. You can use the Generate PSK option or key in your desired key.
Once all details are filled in click on CREATE TUNNEL.
Next, you need to define the local and remote subnets that will be routed through the tunnel.
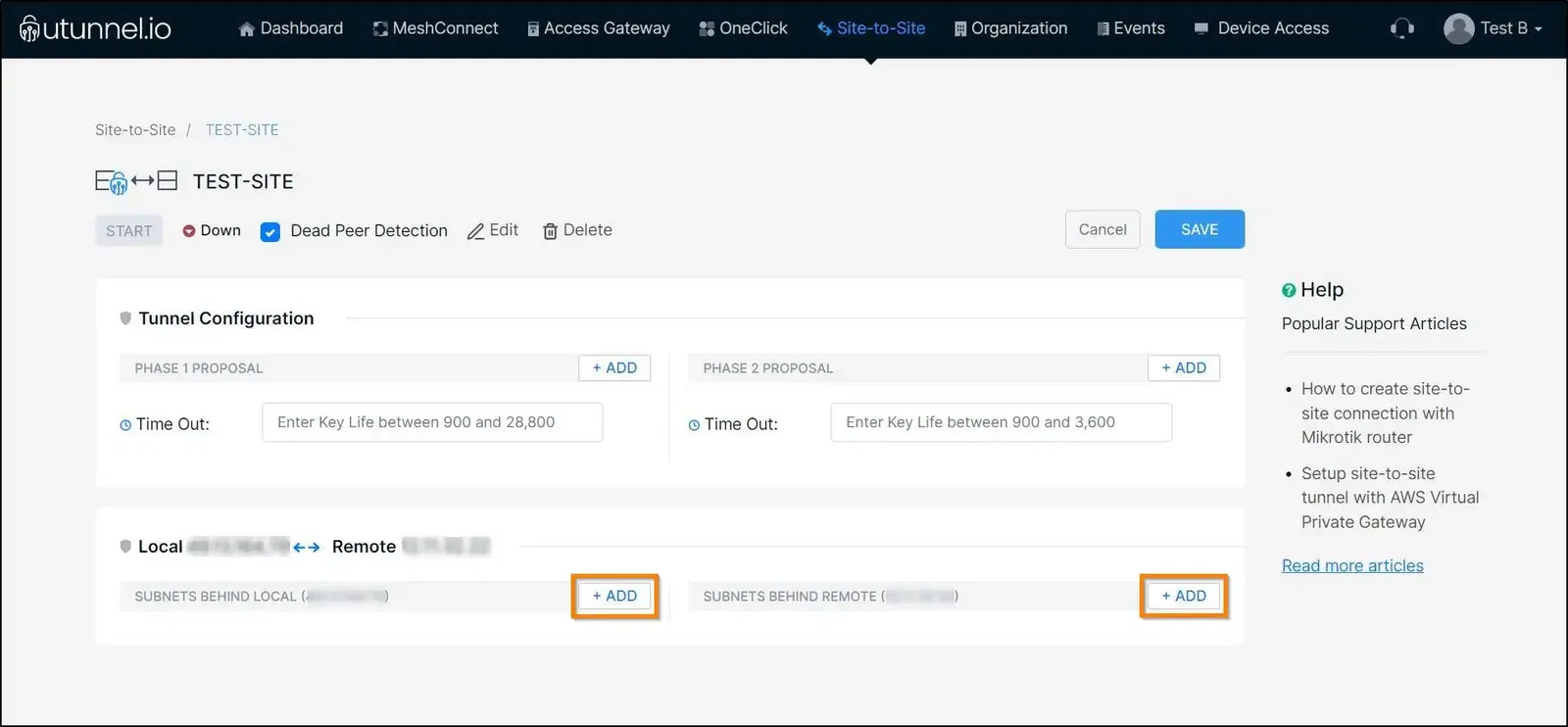
SUBNETS BEHIND LOCAL: Here, you define the networks that are behind UTunnel server.
If you want to route the traffic from the roaming user's devices to the remote subnet through the tunnel, you will need to explicitly define the roaming user's subnets in LOCAL. The default subnets are given below. In case you use custom subnets for roaming VPN users, update it accordingly.
IKEV2 - 172.16.152.0/24
OpenVPN UDP - 172.16.156.0/24
OpenVPN TCP - 172.16.164.0/24
SUBNETS BEHIND REMOTE: Here you define the networks behind Sophos firewall.
Now, you can click on the START button and start with configuring tunnel on Sophos Firewall.
Login to your Sophos firewall with an admin user. Firstly, we need to create a custom IPsec Policy to use with UTunnel tunnel.
For that, click on VPN option on the left side panel and go to IPsec policies on the top right.
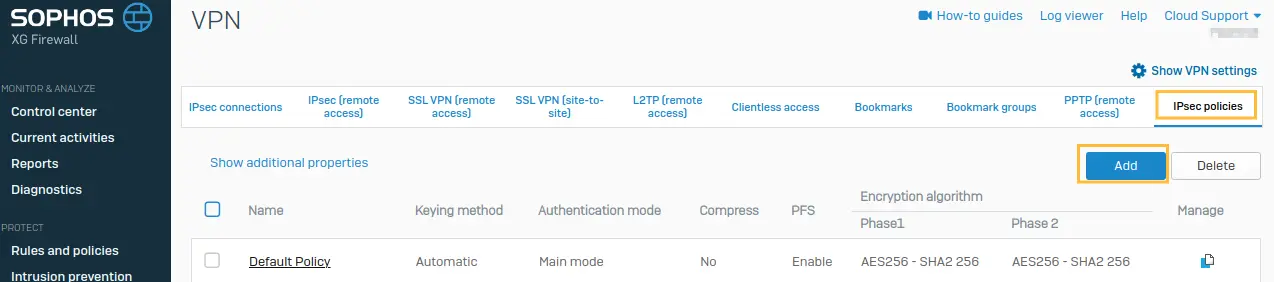
Name the policy as UTN_IKEv2 and select IKEv2 as Key exchange. Set the other configuration parameters as below.
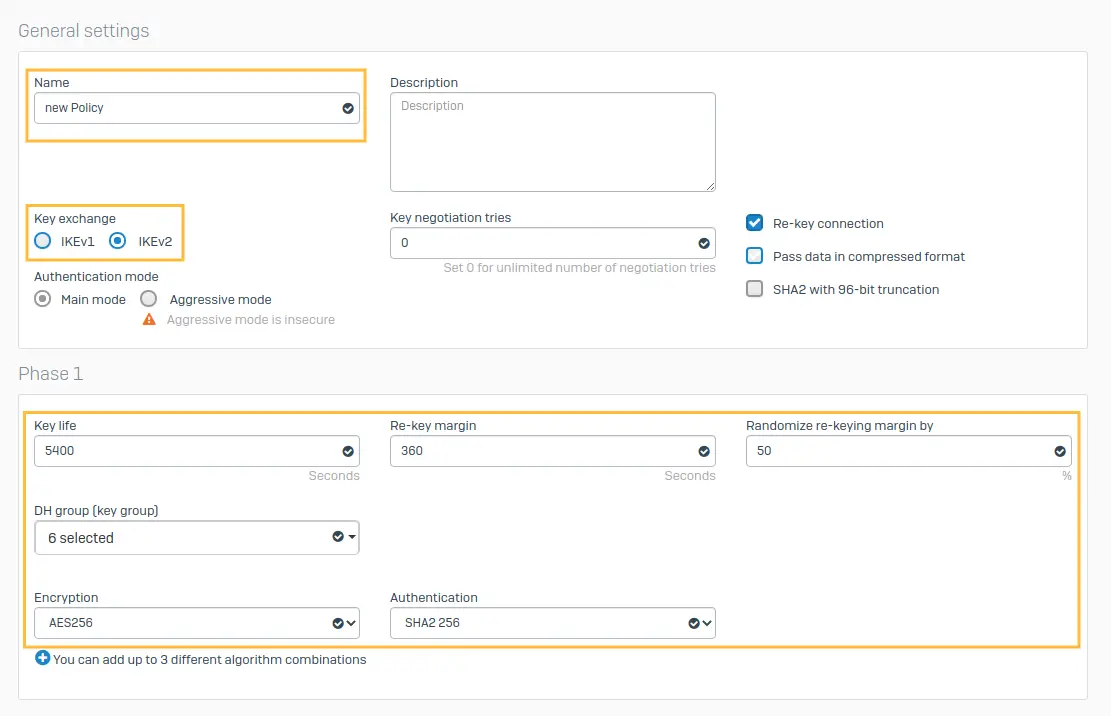
DH group (key group): 14 [DH2048]
Encryption: AES256
Authentication: SHA2 256
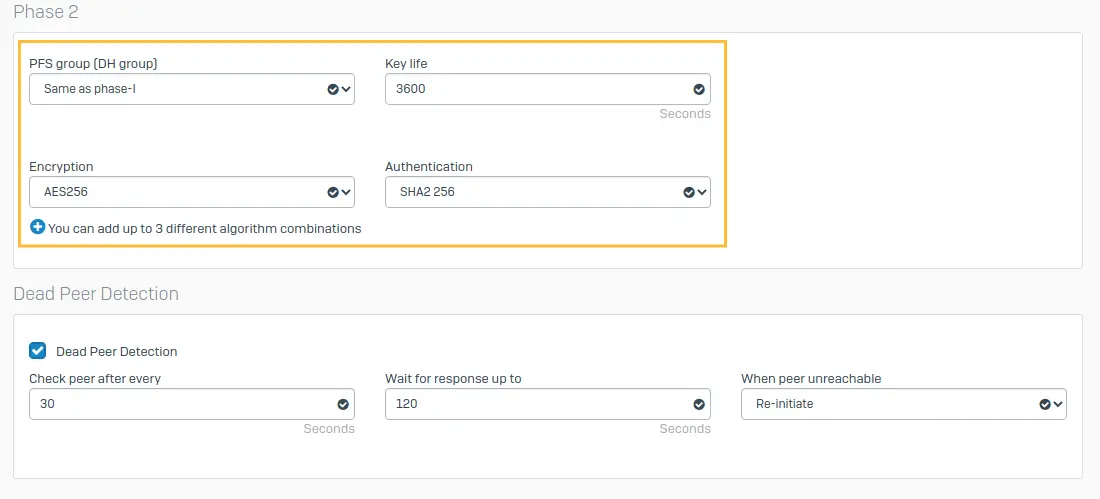
PFS group [DH group]: 14[DH2048]
Keylife: 3600
Encryption: AES256
Authentication: SHA2 256
Click Save.
Now, we have to create the tunnel. Click on VPN option on the left side panel. Navigate to IPsec connections and click on Add button.
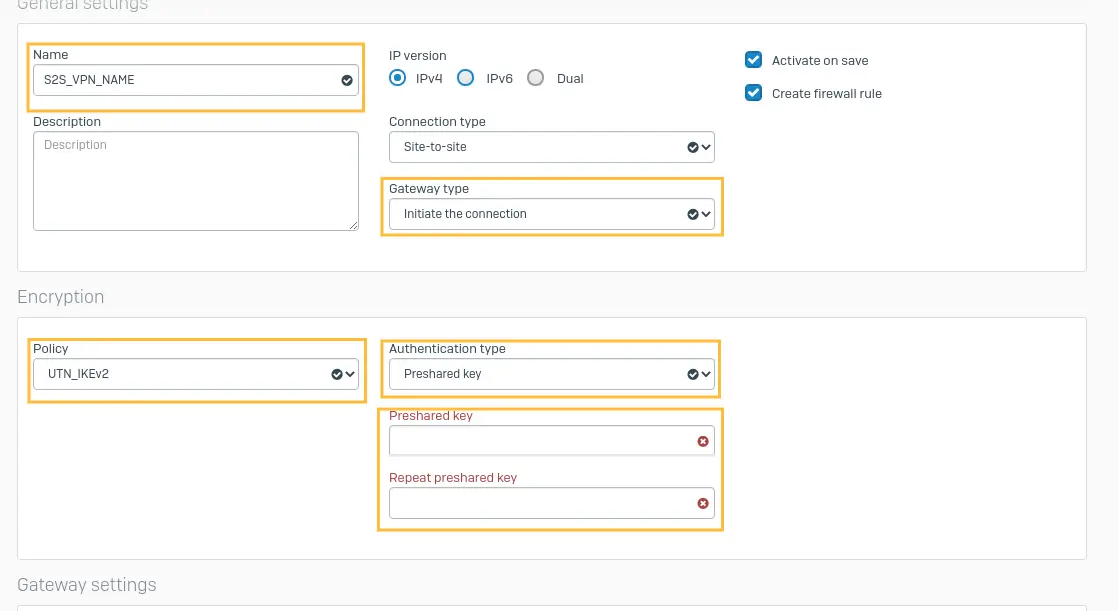
Name: Give a name for the tunnel.
Connection type: Site-to-Site
Gateway type: Initiate the connection
Encryption: IKEv2
Authentication type: Preshared key
And key in the Preshared key that was generated while creating tunnel in UTunnel (you need to use the same PSK on both ends)
Configure Local and Remote gateway settings as explained below.
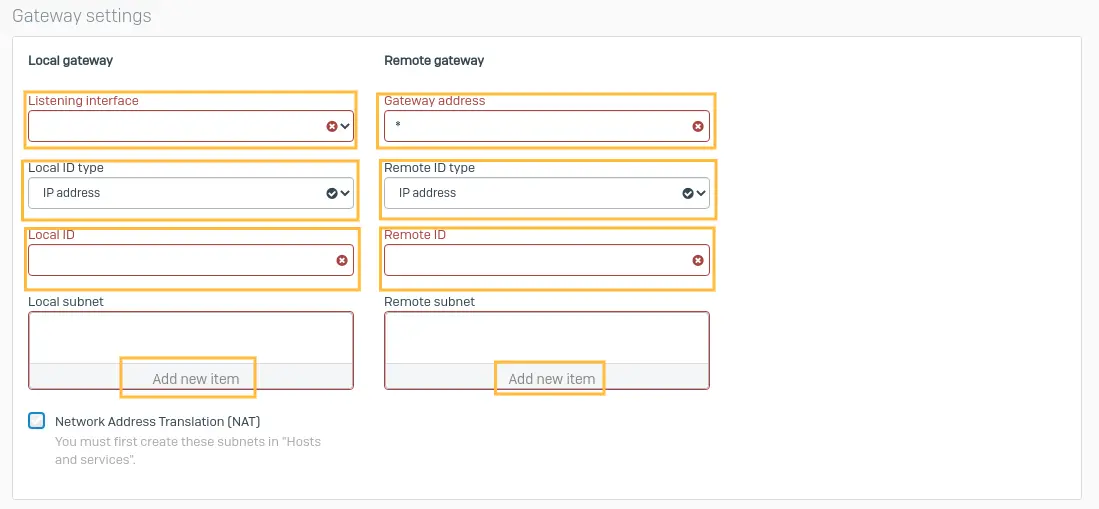
Local gateway settings
Listening interface: Select the appropriate port from the dropdown.
Local ID type: Select IP address
Local ID: Sophos's public IP address configured with the above-selected interface
Local Subnet: Subnets behind the Sophos Firewall
Remote gateway settings
Gateway address: UTunnel server IP Address.
Remote ID type: Select IP address.
Remote ID: UTunnel server IP Address.
Remote subnet: The subnets behind UTunnel server.
Make sure the ‘Create firewall rule’ option is selected, this will create all necessary firewall rules automatically.
Click on Save. The tunnel should be up and running now. If not, restart the tunnel on both sides. We recommend restarting at UTunnel side first always.